Microsoft and Okta are two of the latest victims to had had data stolen by the now-famous group, Lapsus$. They have published a response to their incidents and the tactics used to steal the data. In its blog, Microsoft refers to the group as DEV-0537.
Unlike most activity groups that stay under the radar, DEV-0537 doesn’t seem to cover its tracks. They go as far as announcing their attacks on social media or advertising their intent to buy credentials from employees of target organizations. DEV-0537 also uses several tactics that are less frequently used by other threat actors tracked by Microsoft. Their tactics include phone-based social engineering; SIM-swapping to facilitate account takeover; accessing personal email accounts of employees at target organizations; paying employees, suppliers, or business partners of target organizations for access to credentials and multifactor authentication (MFA) approval; and intruding in the ongoing crisis-communication calls of their targets.
Microsoft confirmed Lapsus$ gained access by compromising an employee’s accounts. The group has released 37 GB of data containing source code Bing and Cortana. For Okta, Lapsus$ posted screenshots claiming it gained access to the authentication and identity management platform’s internal websites. David Bradbury (Okta Chief Security Officer) responded to the claims.
In January 2022, Okta detected an unsuccessful attempt to compromise the account of a customer support engineer working for a third-party provider. As part of our regular procedures, we alerted the provider to the situation, while simultaneously terminating the user’s active Okta sessions and suspending the individual’s account. Following those actions, we shared pertinent information (including suspicious IP addresses) to supplement their investigation, which was supported by a third-party forensics firm.
Following the completion of the service provider’s investigation, we received a report from the forensics firm this week. The report highlighted that there was a five-day window of time between January 16-21, 2022, where an attacker had access to a support engineer’s laptop. This is consistent with the screenshots that we became aware of yesterday.
After a thorough analysis of these claims, we have concluded that a small percentage of customers – approximately 2.5% – have potentially been impacted and whose data may have been viewed or acted upon. We have identified those customers and are contacting them directly. If you are an Okta customer and were impacted, we have already reached out directly by email. We are sharing this interim update, consistent with our values of customer success, integrity, and transparency.
Bradbury is hosting a webinar at 8 a.m. PDT and 4 p.m. PDT. Okta customers can register to attend here.
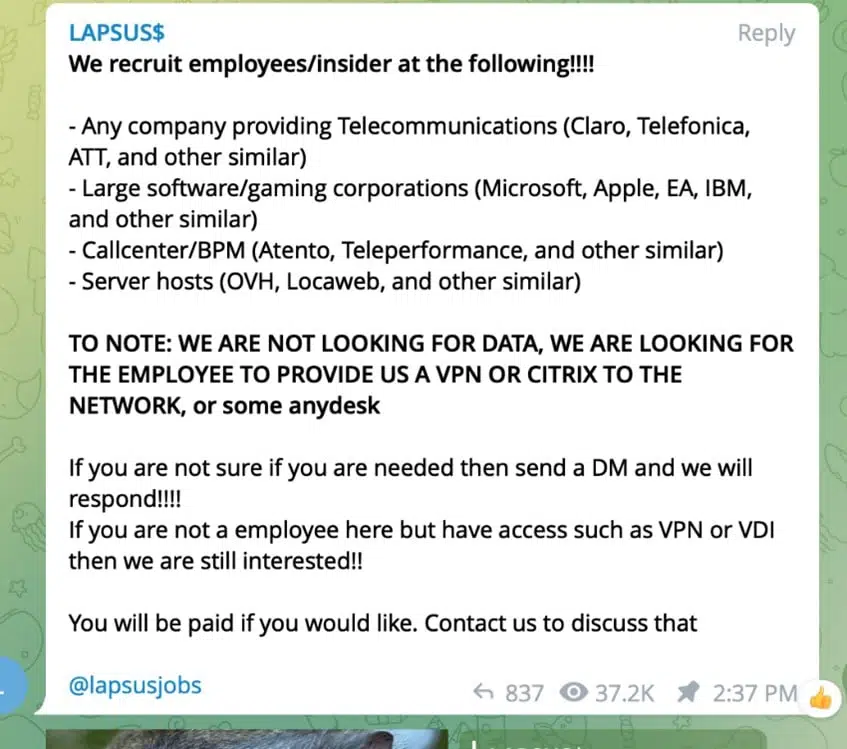
Microsoft has shared more details about the tactics used, including social engineering, password-stealing software, and paying employees of targeted organizations. The group is now looking for those wishing to provide it access to companies.
Microsoft has published the following recommendations to help others.
Do
• Require Multifactor Authenticator for all users coming from all locations including perceived trusted environments, and all internet-facing infrastructure–even those coming from on-premises systems.
• Leverage more secure implementations such as FIDO Tokens, or the Microsoft Authenticator with number matching. Avoid telephony-based MFA methods to avoid risks associated with SIM-jacking.
• Use Azure AD Password Protection to ensure that users aren’t using easily-guessed passwords. Our blog about password spray attacks outlines additional recommendations.
• Leverage passwordless authentication methods such as Windows Hello for Business, Microsoft Authenticator, or FIDO tokens to reduce risks and user experience issues associated with passwords.
Do NOT:
• Use weak MFA factors such as text messages (susceptible to SIM swapping), simple voice approvals, simple push (instead, use number matching), or secondary email addresses.
• Include location-based exclusions. MFA exclusions allow an actor with only one factor for a set of identities to bypass the MFA requirements if they can fully compromise a single identity.
• Allow credential or MFA factor sharing between users.
Require healthy and trusted endpoints
• Require trusted, compliant, and healthy devices for access to resources to prevent data theft.
• Turn on cloud-delivered protection in Microsoft Defender Antivirus to cover rapidly evolving attacker tools and techniques, block new and unknown malware variants, and enhance attack surface reduction rules and tamper protection.