
Bad Packets Report’s Troy Mursch is warning of a severe flaw in Linksys Smart Wi-Fi routers that allows attackers to tap into them remotely and access their complete connection histories. That includes the “MAC address of every device that’s ever connected to it (full historical record, not just active devices),” “device name (such as ‘TROY-PC’ or ‘Mat’s MacBook Pro’),” and “operating system (such as ‘Windows 7’ or ‘Android’).”
All an attacker has to do is go to the router’s public IP address in a web browser, open the developer console, go to the network tab, and then click on the JNAP/ entries. No authentication is required.
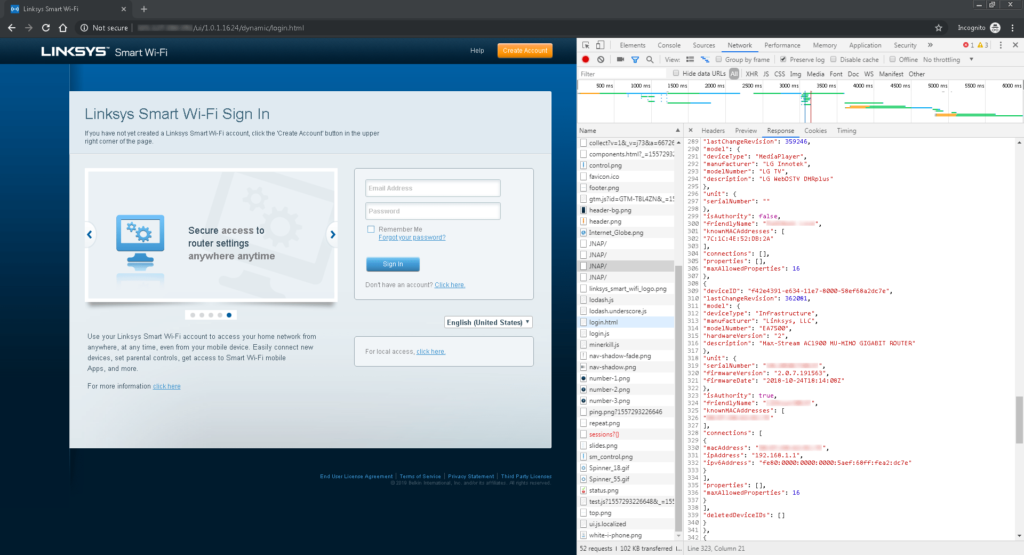
Mursch says all of the following routers are vulnerable, even with the latest firmware updates.
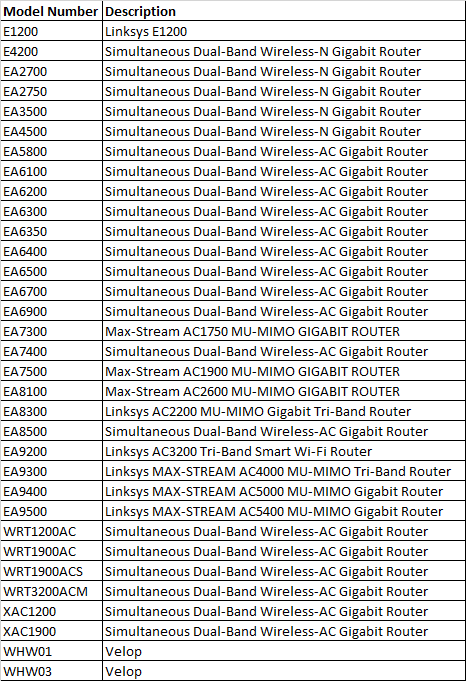
Ars Technica’s coverage notes that Linksys researchers claimed they “couldn’t reproduce the exploit on routers that installed a patch released in 2014,” however.
In any scenario, publicly leaking the historical record of every device that’s ever connected to the Linksys Smart Wi-Fi router is a privacy concern that shouldn’t be taken lightly. This information allows attackers to gain visibility inside your home or business network, enabling them to conduct targeted attacks.
