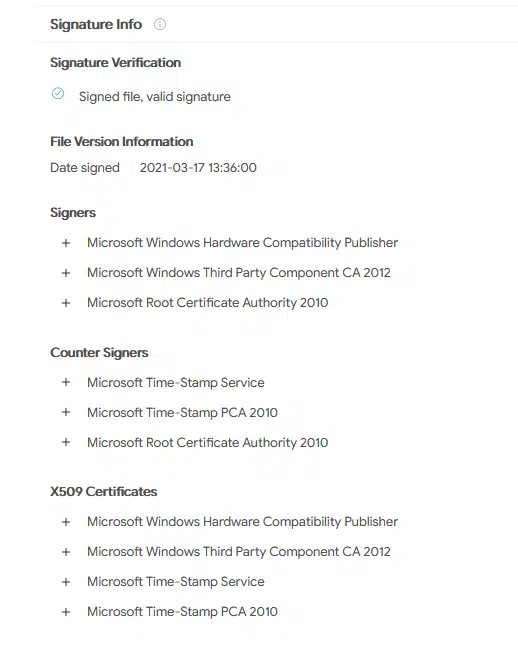
Microsoft has confirmed that it recently signed off on a malicious driver that was being distributed within gaming environments. Dubbed “Netfilter” and initially documented by G DATA malware analyst Karsten Hahn, the malicious driver is a rootkit that raised serious suspicions after it was found communicating with Chinese command-and-control (C2) IPs. Microsoft has clarified that there is no evidence of stolen code-signing certificates being used by the malicious actors, but it still isn’t clear what the company meant by “gaming environments.” All Microsoft has said is that the activity is “limited to the gaming sector specifically in China”; no specific platforms or services are named in its blog post.
The actor’s activity is limited to the gaming sector specifically in China and does not appear to target enterprise environments. We are not attributing this to a nation-state actor at this time. The actor’s goal is to use the driver to spoof their geo-location to cheat the system and play from anywhere. The malware enables them to gain an advantage in games and possibly exploit other players by compromising their accounts through common tools like keyloggers.
Sources: Microsoft, Bleeping Computer, G DATA