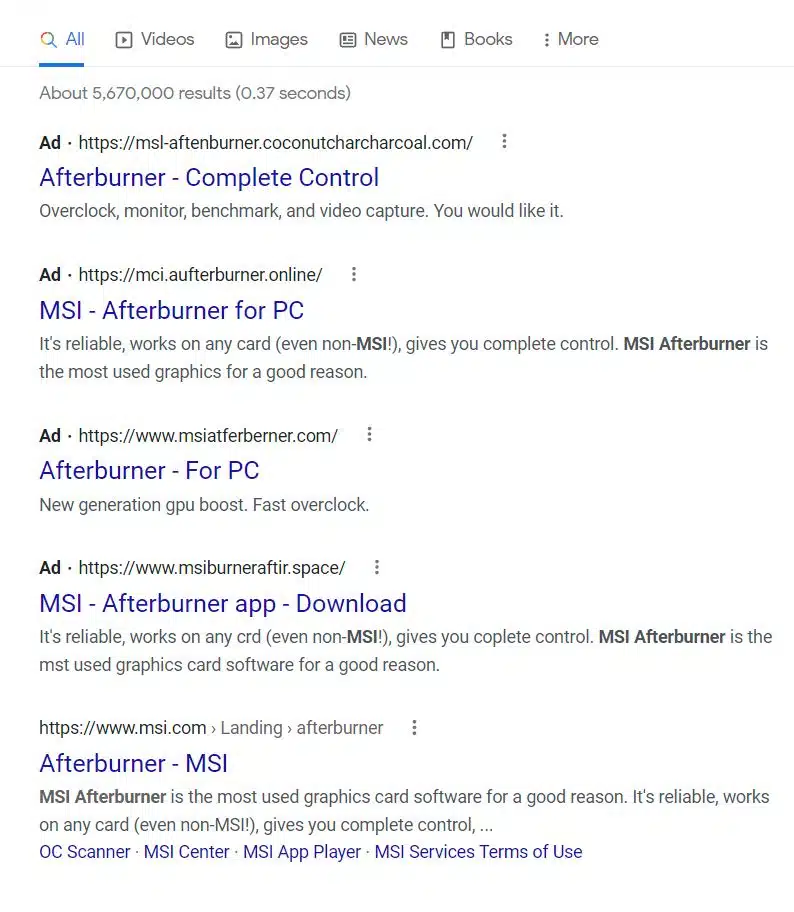
Researchers have discovered that spoofed MSI Afterburner sites have versions of the popular utility that has been injected with mining malware. Cybersecurity specialists at Cyble Research and Intelligence Labs have discovered that the infected software contains code for crypto-mining. At a time known as the season of giving some users may be giving more than they know every time they power up their computers and connect to the internet.
“This coin-miner malware campaign uses MSI Afterburner phishing sites targeting gamers and other individuals who require high-performance computing. TAs use phishing emails, online ads, and various other means to propagate links over the internet. TAs could also target other specialized software to spread malware.”
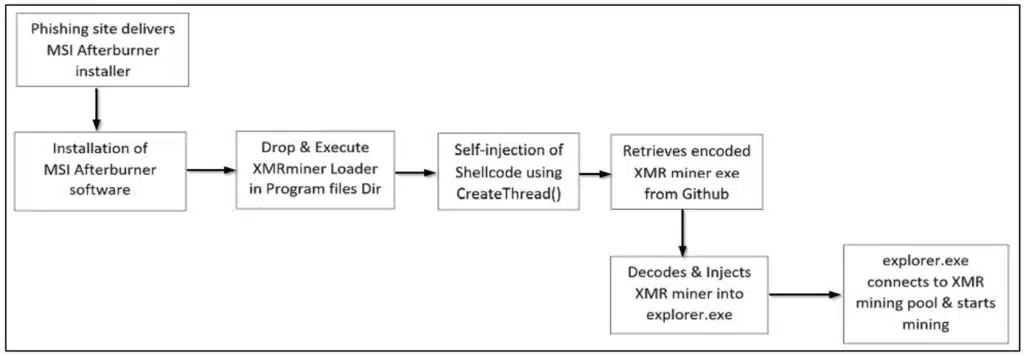
As we can see from a quick search on Google, spoofed MSI Afterburner sites are dominating the search engine with the official site buried at the bottom of the list. The altered software injects code for XMR miner onto the infected machine during the installation process. A file named “browser_assistent.exe” is placed in the “Program files” location and once it executes it injects, and loads, a shellcode of the encoded XMR Miner binary is pulled from the GitHub repository which is then further injected into explore.exe.
“In this case, Afterburner drops the XMR miner for mining which silently abuses the victim’s system resources (CPU and RAM mostly) and produces revenues for attackers. This significantly decreases the victim’s overall system performance and drains their system resources, severely affecting the productivity of the victim user or organization.”
Cyble has advised users to update and run their antivirus software which should help prevent such downloads, or their installation and operation, but also warns against downloading the software from torrent sites or any other beyond the official website. It (Cyble) has a list of indicators of compromise which include installed app names and websites they are connecting to but also advises users to periodically check the systems for performance and CPU usage. Ultimately this serves as a strong reminder to users to only download apps from official sources and to also pay close attention to addresses and names to spot errors indicating a spoofed site.