Researchers have discovered critical Bluetooth vulnerabilities that could potentially affect billions of devices around the world. The newly discovered exploits are categorized as Bluetooth Forward and Future Secrecy Attacks and Defenses, or BLUFFS for short. A researcher at EURECOM published a paper on them detailing how an attacker can utilize a man-in-the-middle (MITM) technique to impersonate a paired device using four flaws in the key derivation process. Once that stage is achieved the attacker can then brute-force attack the device(s) to further decrypt the key for access. The vulnerabilities affect BT 4.2 through the current BT 5.4 version and technically cannot be patched out. However, it’s not all bad news as it’s possible to mitigate the vulnerabilities with increased security settings. The Bluetooth SIG has posted its statement regarding the findings in a new security bulletin.
Per Bluetooth SIG:
“Implementations are advised to reject service-level connections on an encrypted baseband link with key strengths below 7 octets. For implementations capable of always using Security Mode 4 Level 4, implementations should reject service-level connections on an encrypted baseband link with a key strength below 16 octets. Having both devices operating in Secure Connections Only Mode will also ensure sufficient key strength.”
“Implementations should also track that a link key was established using BR/EDR Secure Connections in the Bluetooth Security Database and verify that any subsequent encryption establishment also uses Secure Connections. If encryption was not established in Secure Connections mode for a bonded peer that previously bonded using Secure Connections mode or if the negotiated encryption key size is too small, the link should be terminated.”
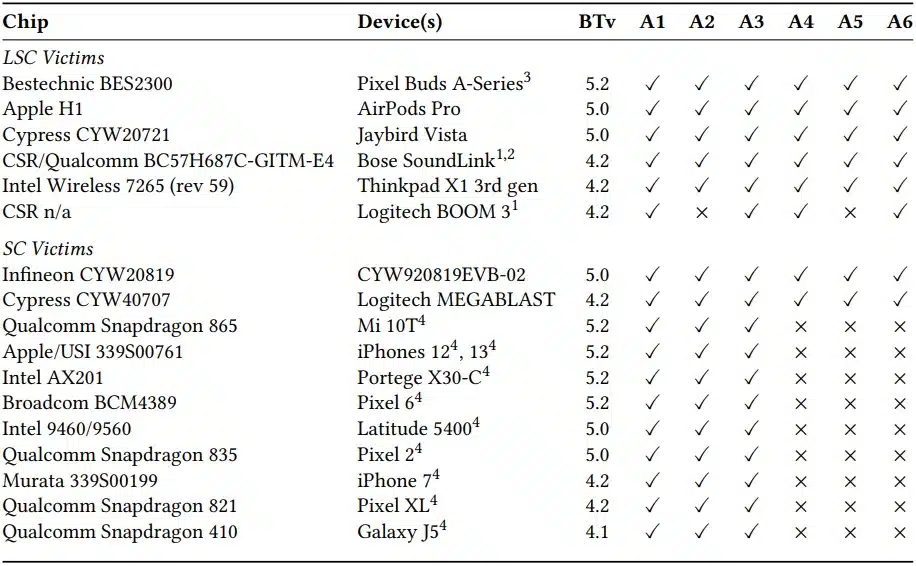
The paper demonstrates how six scenarios can be employed to enact the attack and once successful, can allow future access to compromised devices without user interaction unless proper settings have been applied. Device test results showed how at least three scenarios were successful across a wide range of devices using BT version 4.1 – 5.2. Since these exploits are based on the BT standard it means that any OS can be vulnerable and any devices using the mentioned versions of Bluetooth could be exploited.
Per EURECOM:
“This paper presents the first security evaluation of Bluetooth forward and future secrecy guarantees. It uncovers two new vulnerabilities in Bluetooth’ssession establishment, enabling to reuse of a weak
session key across sessions. We show how to exploit these flaws in six attack scenarios to impersonate and MitM arbitrary devices across sessions. Our attacks break Bluetooth’s forward and future secrecy as they compromise past and future encrypted messages with novel key reuse attacks. Our findings result from experiments with Bluetooth session establishment on actual devices and inference from the standard. We focused on 𝑆𝐾 as, unlike 𝑃𝐾, it can be targeted without user interaction, and its entropy can be lowered without violating the standard.”
The following mitigations have been recommended by the researchers to prevent future versions of Bluetooth from being affected by BLUFFS.
Per Bleeping Computer:
- Introduce a new “Key Derivation Function” (KDF) for Legacy Secure Connections (LSC) that involves mutual nonce exchange and verification, adding minimal overhead.
- Devices should use a shared pairing key for the mutual authentication of key diversifiers, ensuring the legitimacy of session participants.
- Enforce Secure Connections (SC) mode where possible.
- Maintain a cache of session key diversifiers to prevent reuse.