
Apple network traffic took a brief 12-hour detour through the Russian Rostelecom network that spanned July 26-27. Reports state that Rostelcom began announcing routes for Apple’s network Tuesday evening in what is referred to as a BGP (Border Gateway Protocol) hijack.
Around 21:25 UTC On 26 July 2022, Rostelecom’s AS12389 network started announcing 17.70.96.0/19. This prefix is part of Apple’s 17.0.0.0/8 block; usually, Apple only announces the larger 17.0.0.0/9 block and not this shorter prefix length.
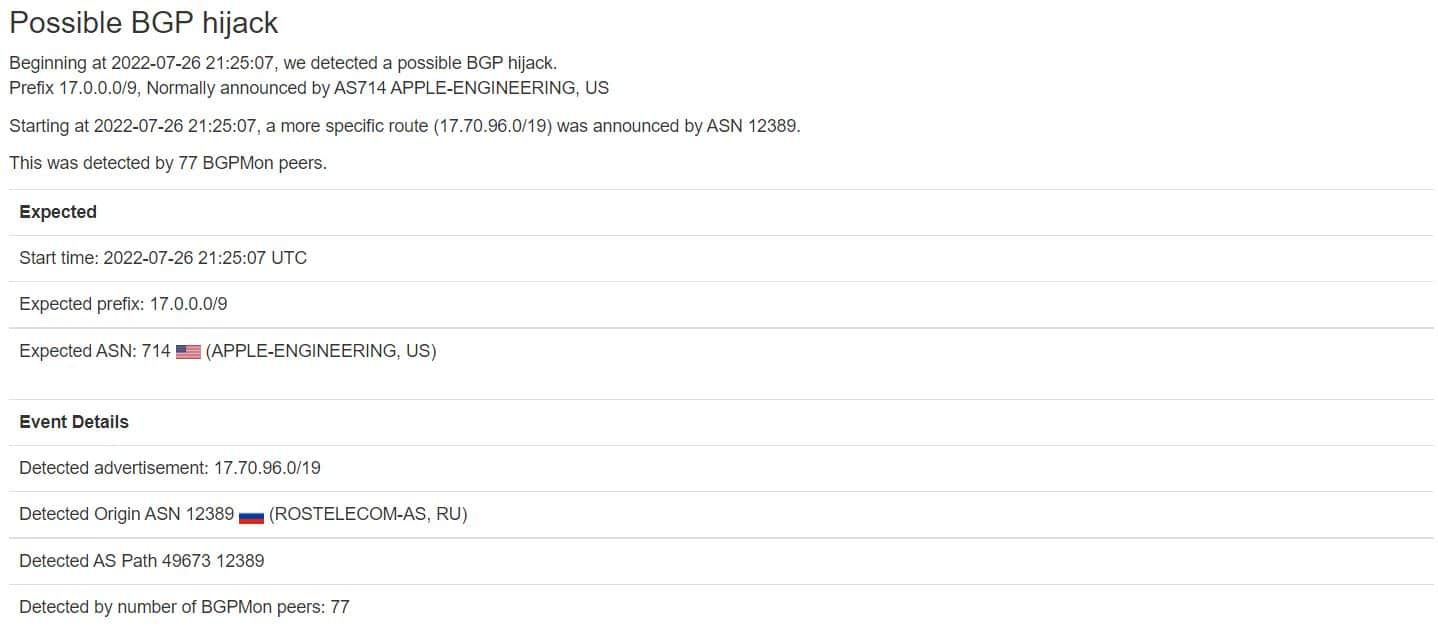
Aftab Siddiqui (MANRS Internet Society senior internet technology manager) said this is not the first time that Rostelecom was involved in a BGP hijack as another happened in 2020 involving Amazon and many others.
To get more information, I looked up all the announcements from AS12389 with the AS_PATH “20764 12389”. I used Isolario.it bgpdump, as it has more peers than route-views. Instantly there were several hits (4569 unique announcements) and none of them belonged to AS12389. Hurricane Electric’s BGP Toolkit also noted a similar number (4567).
Out of those 4569 prefixes, 4255 belong to Amazon(AS16509 and AS14618), 85 belong to Akamai (AS20940, AS16625), and the rest belong to several different service providers including Level3, Alibaba, Digital Ocean, Linode, and others.
Clearly, Rostelecom (AS12389) has experience with BGP hijacking but it is not known what data may have been extracted from the Apple network traffic or what services may have been impacted during that period. Mr. Siddiqui went on to say that “When the routes a network is announcing are not covered by valid Route Origin Authorization (ROA), the only option during a route hijack is to announce more specific routes.” Apple networking engineers did start announcing a more specific range of routing addresses 5 hours after CISCO BGPStream reported on the possible hijack but AS12389 did not cease its broadcasts until roughly 09:39 UTC on July 27. So far, Apple has not responded to requests regarding the incident.
The Register asked MANRS whether anyone there had heard anything from Apple since its post was published and a spokesperson replied, “We have not heard anything from Apple yet on this issue. The MANRS team is reaching out privately to learn more about the incident.”
Source: MANRS (via The Register)
